|
|
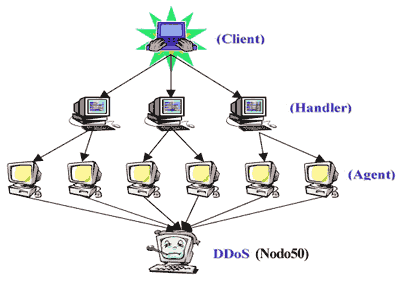
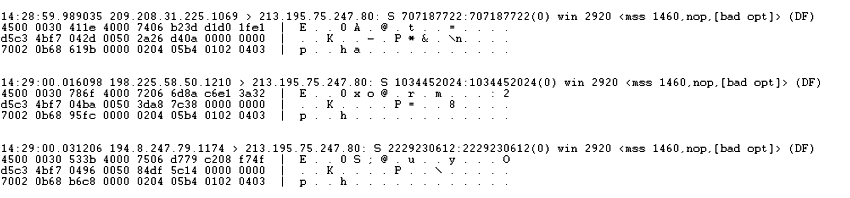
Nodo50: Demanding our right to communicate freely 18th of January of 2002 http://www.nodo50.org/criminalizacion_mov_sociales/nodo50 ayuda@nodo50.org Post a message in our message board иииии> On Thursday 17th of January, 2002, Nodo50 suffered a denial of service attack aimed at our Web Server. This anonymous action meant that the WebSites of over 400 organisations hosted by Nodo50 (http://www.nodo50.org/organi.php?x=%) were inaccessible for 18 hours, to site owners and to the thousands of people who visit the sites daily. The Assembly of Nodo50 considers the mass media's recent coverage of the work of the "Network of Counterinformation EU 2002" (1) to be an attempt by law enforcement and mainstream media to criminalize legitimate work, misinform the public and engineer an atmosphere encouraging the type of attack Nodo50 has experienced. The original report was published by the Colpisa agency and can be found here: http://www.nodo50.org/criminalizacion_mov_sociales/nodo50/colpisa.htm It is not the first time that law enforcement and journalists have come together to generate such an environment. Nor is it the first time that Nodo50 has been the target of such attacks. It is common here for this mix of ghosts and misinformation to aim to turn public opinion against perfectly legitimate and legal actions through insinuations of criminal activitiy. People have the right to inform and to inquire freely and thus protect against attempts to seed a cycle of suspicion that encourages justification for attacks such as we have experienced. Considering that Spain has recently taken up presidency of the European Union, we are aware that this will not be the last attack. The Spanish Government will attempt to continue with actions that repress legitimate actions of people and organisations opposed to their policies and positions, in the interest of protecting and representing interests of Bankers and multinationals in Europe. To identify our political work with those they label "the violent ones" is a self-interested simplification of the work of thousands of organizations who communicate through the Nodo50 network. We will continue fighting for our right to communicate and express ourselves freely. Though our means may be modest, we will continue with absolute firmness and conviction. Assembly of Nodo50 |